Learn API Testing!
This is a deliberately vulnerable app built for learning.
🔐 Get an Access Token (cURL Format)
>> Use these curl commands in your terminal to register and login :
# Register a new user
curl -X POST https://tarkash.surapura.in/api/register \
-H "Content-Type: application/json" \
-d '{"username": "masino", "password": "tamburo"}'
# Login to get JWT token
curl -X POST https://tarkash.surapura.in/api/login \
-H "Content-Type: application/json" \
-d '{"username": "masino", "password": "tamburo"}'
> The response will look like:
{"token":"your-jwt-token"}
> Save the token. Use it as a Bearer token for all other requests.
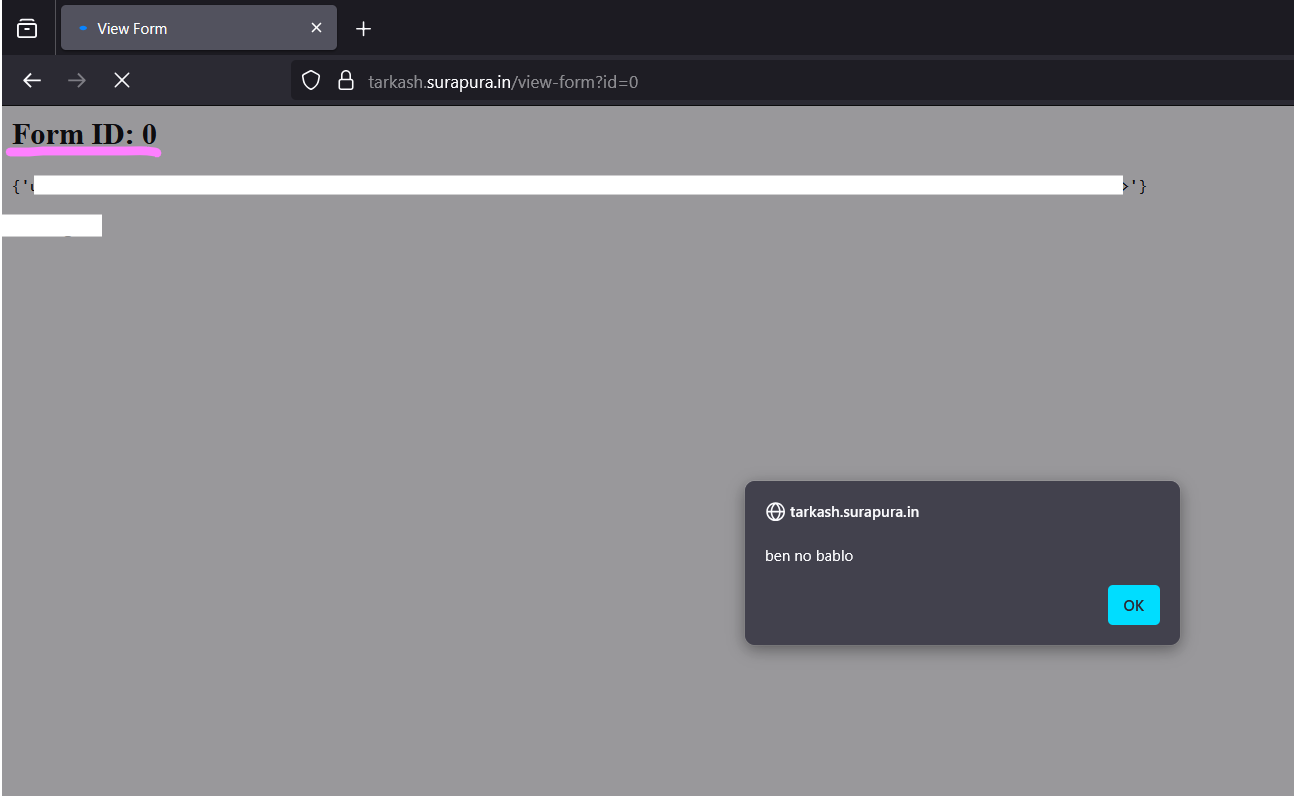
# Submit a Form (Find the special id=0 flag!)
curl -X PUT "https://tarkash.surapura.in/api/form?id=0" \
-H "Authorization: Bearer YOUR_JWT_TOKEN_HERE" \
-H "Content-Type: application/json" \
-d '{"username":"masino","name":"tamburo","email":"bhootnike","message":"ben no bablo"}'
> Explore and tamper with id=0. Understand response logic, bypasses, and constraints
# File Upload Endpoint
curl -X POST "https://tarkash.surapura.in/api/upload" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer YOUR_JWT_TOKEN_HERE" \
-F "file=@/path/to/your/file.jpg"
> Visit: https://tarkash.surapura.in/uploads/yourfile.jpg
🧠 Practice Flow
- Step 1: Register at
https://tarkash.surapura.in/api/registerwith a JSON body like{"username": "test", "password": "pass"} - Step 2: Login via
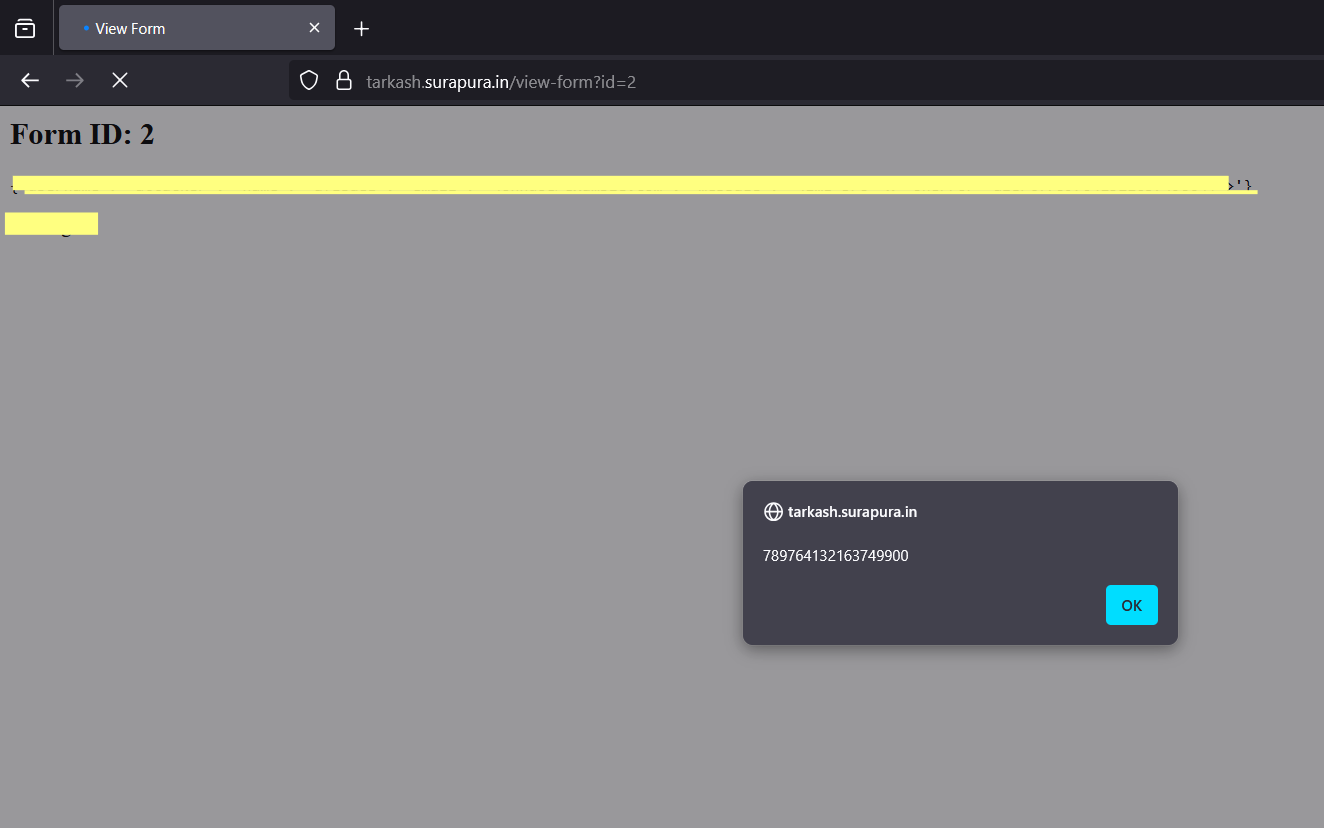
/api/loginand receive your JWT token - Step 3: Submit a form with a
messagefield to/api/form - Step 4: View / Edit submitted forms via
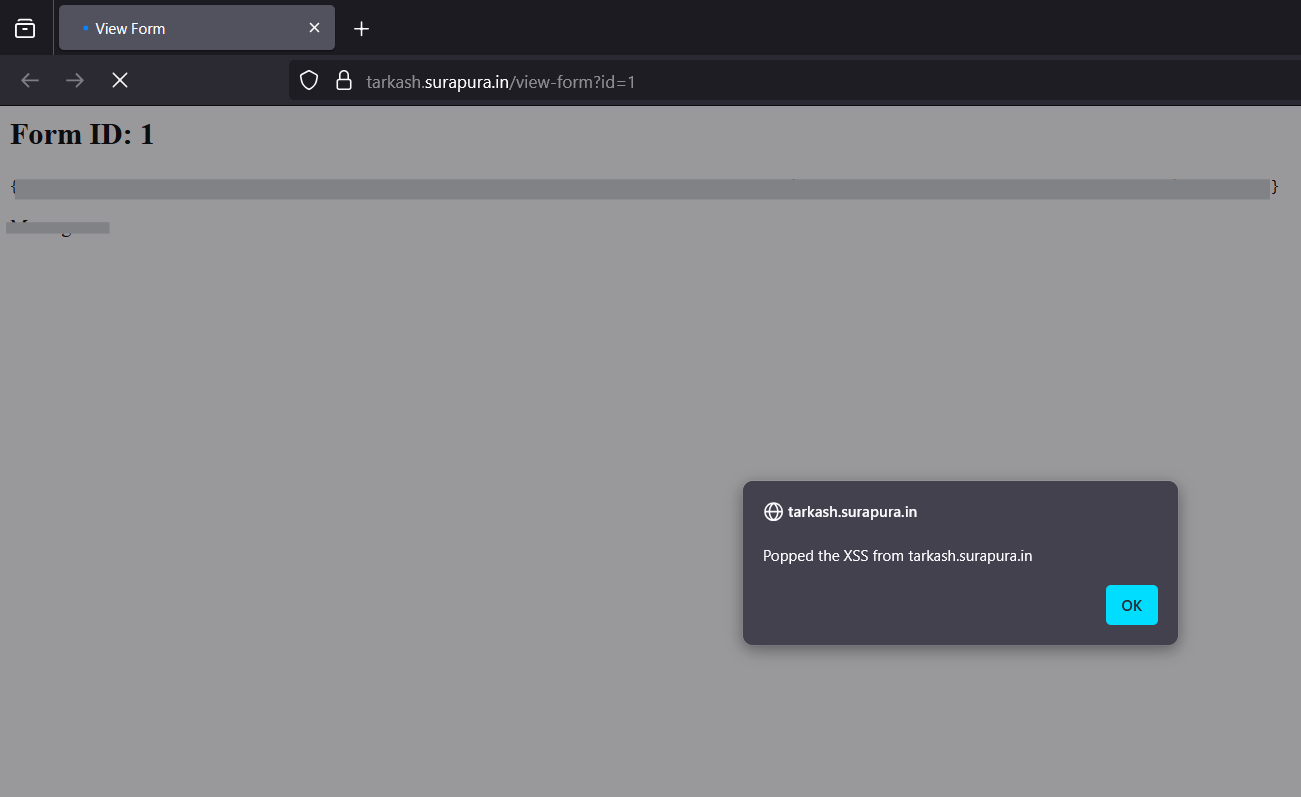
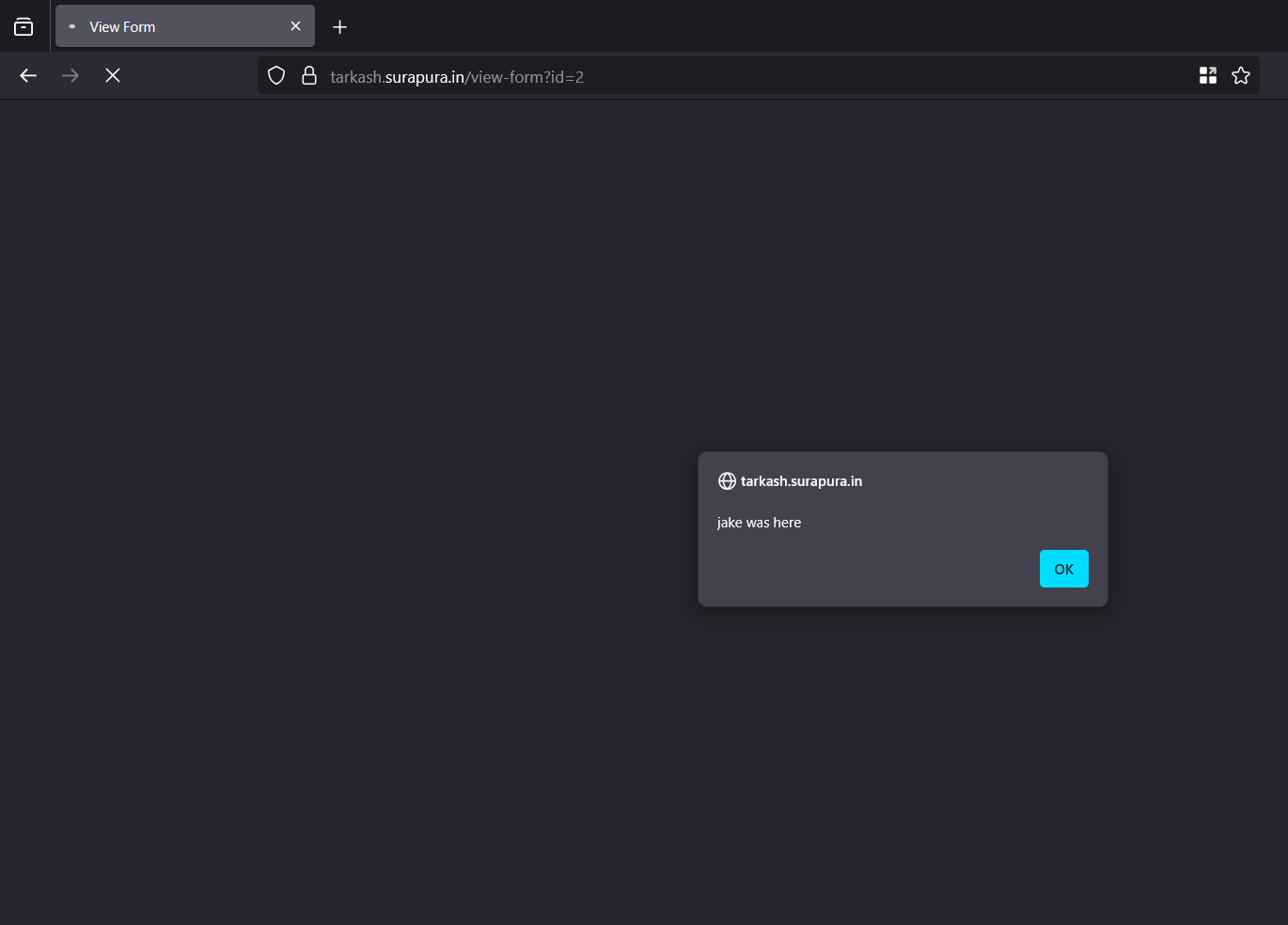
/api/form?id=1and exploit IDOR and stored XSS - Step 5: Visit
/view-form?id=1to render and trigger your payload (stored XSS)
> POP that XSS
> submit form with id=0
Need help solving or have a query? Contact: ikajakam